Krebs - Booter Boss Interviewed in 2014 Pleads Guilty
A 20-year-old Illinois man has pleaded guilty to running multiple DDoS-for-hire services that launched millions of attacks over several years. The plea deal comes almost exactly five years after KrebsOnSecurity interviewed both the admitted felon and his father and urged the latter to take a more active interest in his son’s online activities.
Sergiy P. Usatyuk of Orland Park, Ill. pleaded guilty this week to one count of conspiracy to cause damage to Internet-connected computers and for his role in owning, administering and supporting illegal “booter” or “stresser” services designed to knock Web sites offline, including exostress[.]in, quezstresser[.]com, betabooter[.]com, databooter[.]com, instabooter[.]com, polystress[.]com and zstress[.]net.
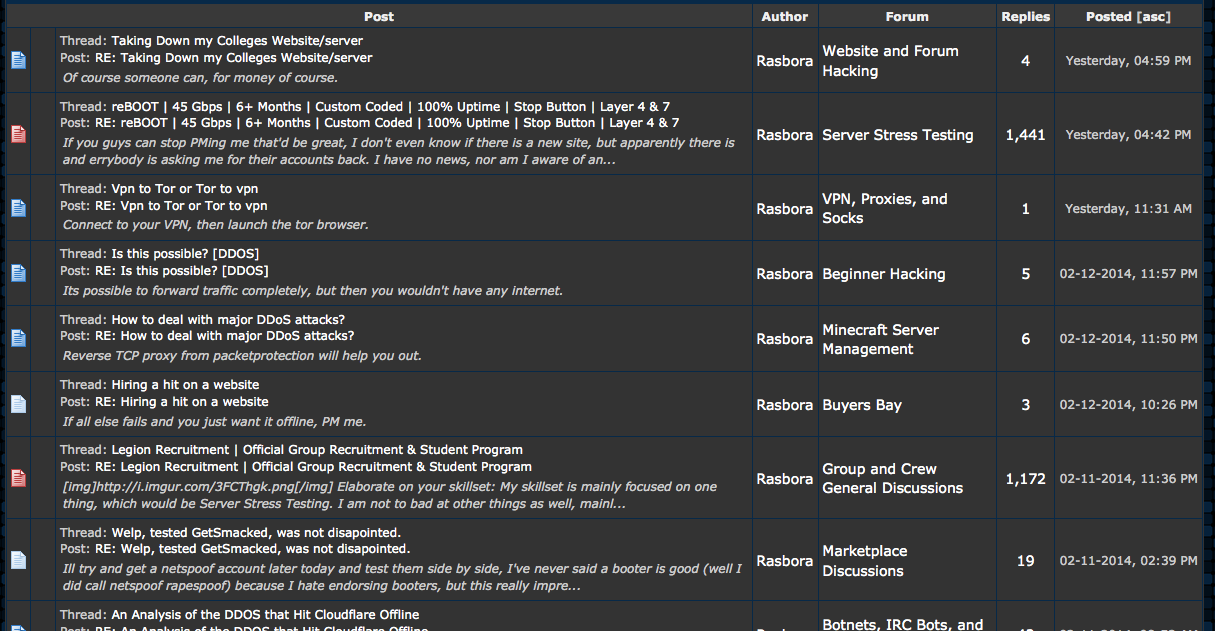
Some of Rasbora’s posts on hackforums[.]net prior to our phone call in 2014. Most of these have since been deleted.
A U.S. Justice Department press release on the guilty plea says Usatyuk — operating under the hacker aliases “Andrew Quez” and “Brian Martinez” — admitted developing, controlling and operating the aforementioned booter services from around August 2015 through November 2017. But Usatyuk’s involvement in the DDoS-for-hire space very much predates that period.
In February 2014, KrebsOnSecurity reached out to Usatyuk’s father Peter Usatyuk, an assistant professor at the University of Illinois at Chicago. I did so because a brief amount of sleuthing on Hackforums[.]net revealed that his then 15-year-old son Sergiy — who at the time went by the nicknames “Rasbora” and “Mr. Booter Master” — was heavily involved in helping to launch crippling DDoS attacks.
I phoned Usatyuk the elder because Sergiy’s alter egos had been posting evidence on Hackforums and elsewhere that he’d just hit KrebsOnSecurity.com with a 200 Gbps DDoS attack, which was then considered a fairly impressive DDoS assault.
“I am writing you after our phone conversation just to confirm that you may call evening time/weekend to talk to my son Sergio regarding to your reasons,” Peter Usatyuk wrote in an email to this author on Feb. 13, 2014. “I also have [a] major concern what my 15 yo son [is] doing. If you think that is any kind of illegal work, please, let me know.”
That 2014 story declined to quote Rasbora by name because he was a minor, but his father seemed alarmed enough about my inquiry that he insisted his son speak with me about the matter.
Here’s what I wrote about Sergiy at the time:
Rasbora’s most recent project just happens to be gathering, maintaining huge “top quality” lists of servers that can be used to launch amplification attacks online. Despite his insistence that he’s never launched DDoS attacks, Rasbora did eventually allow that someone reading his posts on Hackforums might conclude that he was actively involved in DDoS attacks for hire.
“I don’t see what a wall of text can really tell you about what someone does in real life though,” said Rasbora, whose real-life identity is being withheld because he’s a minor. This reply came in response to my reading him several posts that he’d made on Hackforums not 24 hours earlier that strongly suggested he was still in the business of knocking Web sites offline: In a Feb. 12 post on a thread called “Hiring a hit on a Web site” that Rasbora has since deleted, he tells a fellow Hackforums user, “If all else fails and you just want it offline, PM me.”
Rasbora has tried to clean up some of his more self-incriminating posts on Hackforums, but he remains defiantly steadfast in his claim that he doesn’t DDoS people. Who knows, maybe his dad will ground him and take away his Internet privileges.
I’m guessing young Sergiy never had his Internet privileges revoked, nor did he heed advice to use his skills for less destructive activities. His dad hung up on me when I called Wednesday evening requesting comment.
Court documents (PDF) related to his case indicate Sergiy Usatyuk and an unnamed co-conspirator earned nearly $550,000 launching some 3.8 million attacks through their various DDoS-for-hire services. The government says he ran the booter services through a Delaware corporation called “OkServers LLC,” which routinely ignored abuse complaints and as such effectively operated as a “bulletproof” hosting company — despite Sergiy’s claims to the contrary.
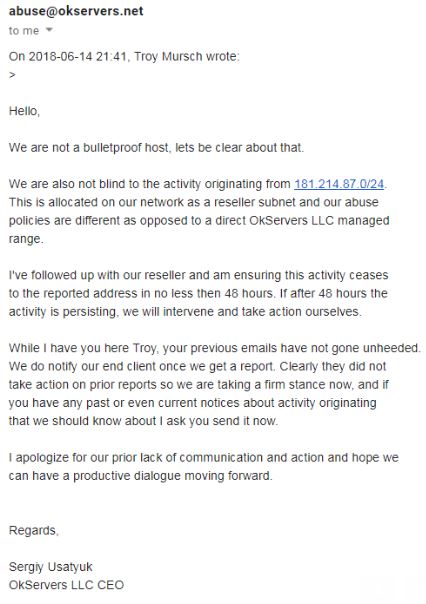
Here’s Sergiy’s response to multiple abuse complaints about OKServers filed in the summer of 2018 by Troy Mursch, chief research officer at Bad Packets LLC.
Sergiy’s guilty plea comes amid a major crackdown by the FBI and the Justice Department on booter services and their operators. In December 2018, the DOJ brought charges against three men as part of an unprecedented, international takedown targeting 15 different booter sites.
According to the government, the use of booter and stresser services to conduct attacks is punishable under both wire fraud laws and the Computer Fraud and Abuse Act (18 U.S.C. § 1030), and may result in arrest and prosecution, seizure of computers or other electronics, significant prison sentences, and a penalty or fine.
from Krebs on Security https://krebsonsecurity.com/2019/02/booter-boss-interviewed-in-2014-pleads-guilty/
Comments
Post a Comment