Krebs - Feds Target $100M ‘GozNym’ Cybercrime Network
Law enforcement agencies in the United States and Europe today unsealed charges against 11 alleged members of the GozNym malware network, an international cybercriminal syndicate suspected of stealing $100 million from more than 41,000 victims with the help of a stealthy banking trojan by the same name.
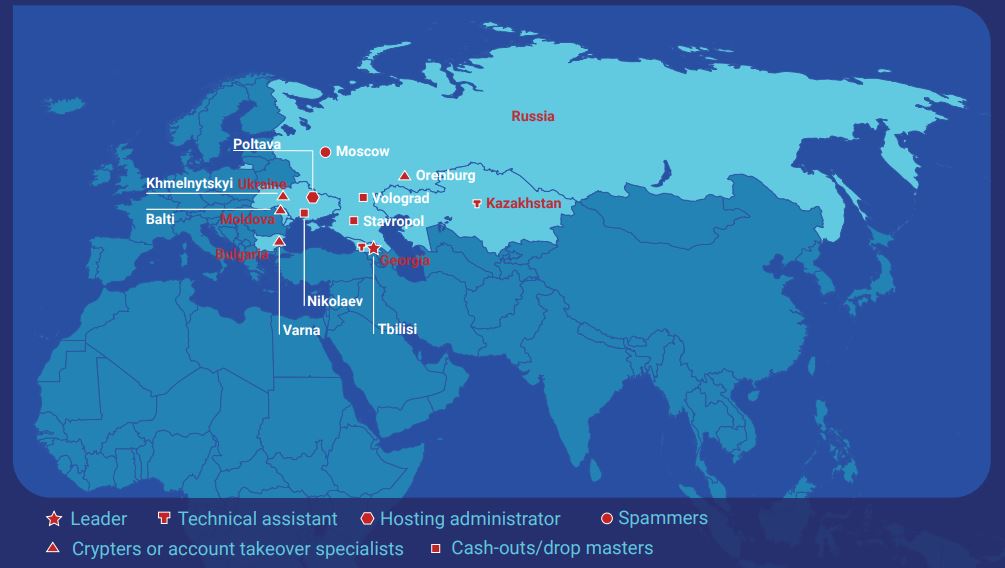
The locations of alleged GozNym cybercrime group members. Source: DOJ
The indictments unsealed in a Pennsylvania court this week stem from a slew of cyber heists carried out between October 2015 and December 2016. They’re also related to the 2016 arrest of Krasimir Nikolov, a 47-year-old Bulgarian man who was extradited to the United States to face charges for allegedly cashing out bank accounts that were compromised by the GozNym malware.
Prosecutors say Nikolov, a.k.a. “pablopicasso,” “salvadordali,” and “karlo,” was key player in the GozNym crime group who used stolen online banking credentials captured by GozNym malware to access victims’ online bank accounts and attempt to steal their money through electronic funds transfers into bank accounts controlled by fellow conspirators.
According to the indictment, the GozNym network exemplified the concept of ‘cybercrime as a service,’ in that the defendants advertised their specialized technical skills and services on underground, Russian-language, online criminal forums. The malware was dubbed GozNym because it combines the stealth of a previous malware strain called Nymaim with the capabilities of the powerful Gozi banking trojan.
The feds say the ringleader of the group was Alexander Konovolov, 35, of Tbilisi, Georgia, who controlled more than 41,000 victim computers infected with GozNym and recruited various other members of the cybercrime team.
Vladimir Gorin, a.k.a “Voland,” “mrv,” and “riddler,” of Orenburg, Russia allegedly was a malware developer who oversaw the creation, development, management, and leasing of GozNym.
The indictment alleges 32-year-old Eduard Malancini, a.k.a. “JekaProf” and “procryptgroup” from Moldova, specialized in “crypting” or obfuscating the GozNym malware to evade detection by antivirus software.
Four other men named in the indictment were accused of recruiting and managing “money mules,” willing or unwitting people who can be used to receive stolen funds on behalf of the criminal syndicate. One of those alleged mule managers — Farkhad Rauf Ogly Manokhim (a.k.a. “frusa”) of Volograd, Russia was arrested in 2017 in Sri Lanka on an international warrant from the United States, but escaped and fled back to Russia while on bail awaiting extradition.
Also charged was 28-year-old Muscovite Konstantin Volchkov, a.k.a. “elvi,” who allegedly provided the spamming service used to disseminate malicious links that tried to foist GozNym on recipients who clicked.
The malicious links referenced in those spam emails were served via the Avalanche bulletproof hosting service, a distributed, cloud-hosting network that for seven years was rented out to hundreds of fraudsters for use in launching malware and phishing attacks. Avalanche was dismantled in Dec. 2016 by a similar international law enforcement action.
The alleged administrator of the Avalanche bulletproof network — 36-year-old Gennady Kapkanov from Poltova, Ukraine — has eluded justice in prior scrapes with the law: During the Avalanche takedown in Dec. 2016, Kapkanov fired an assault rifle at Ukrainian police who were trying to raid his apartment.
After that incident, Ukrainian police arrested Kapkanov and booked him on cybercrime charges. But a judge later ordered him to be released, saying the prosecution had failed to file the proper charges. The Justice Department says Kapkanov is now facing prosecution in Ukraine for his role in providing bulletproof hosting services to the GozNym criminal network.
The five Russian nationals charged in the case remain at large. The FBI has released a “wanted” poster with photos and more details about them. The Justice Department says it is working with authorities in Georgia, Ukraine and Moldova to build prosecutions against the defendants in those countries.
Nikolov entered a guilty plea in federal court in Pittsburgh on charges relating to his participation in the GozNym conspiracy on April 10, 2019. He is scheduled to be sentenced on Aug. 30, 2019.
It’s good to see this crime network being torn apart, even if many of its key members have yet to be apprehended. These guys caused painful losses for many companies — mostly small businesses — that got infected with their malware. Their activities and structure are remarkably similar to that of the “Jabberzeus” crime gang in Ukraine that siphoned $70 million – out of an attempted $220 million — from hundreds of U.S.-based small to mid-sized businesses several years ago.
The financial losses brought about by that gang’s string of cyberheists — or at least the few dozen heists documented in my series Target: Small Business — often caused victim companies to lay off employees, and in some cases go out of business entirely.
A copy of the GozNym indictment is here (PDF).
from Krebs on Security https://krebsonsecurity.com/2019/05/feds-target-100m-goznym-cybercrime-network/
Comments
Post a Comment