Krebs - From Cybercrime Saul Goodman to the Russian GRU
In 2021, the exclusive Russian cybercrime forum Mazafaka was hacked. The leaked user database shows one of the forum’s founders was an attorney who advised Russia’s top hackers on the legal risks of their work, and what to do if they got caught. A review of this user’s hacker identities shows that during his time on the forums he served as an officer in the special forces of the GRU, the foreign military intelligence agency of the Russian Federation.
Launched in 2001 under the tagline “Network terrorism,” Mazafaka would evolve into one of the most guarded Russian-language cybercrime communities. The forum’s member roster includes a Who’s Who of top Russian cybercriminals, and it featured sub-forums for a wide range of cybercrime specialities, including malware, spam, coding and identity theft.
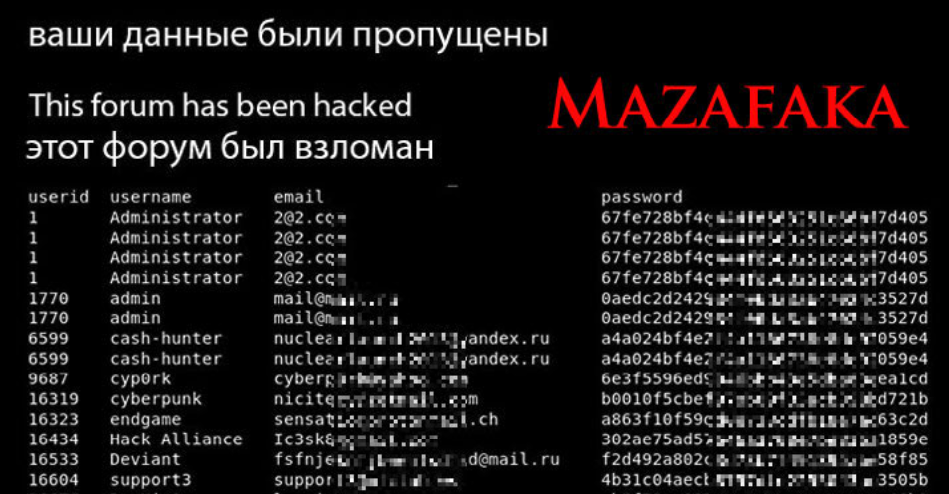
One representation of the leaked Mazafaka database.
In almost any database leak, the first accounts listed are usually the administrators and early core members. But the Mazafaka user information posted online was not a database file per se, and it was clearly edited, redacted and restructured by whoever released it. As a result, it can be difficult to tell which members are the earliest users.
The original Mazafaka is known to have been launched by a hacker using the nickname “Stalker.” However, the lowest numbered (non-admin) user ID in the Mazafaka database belongs to another individual who used the handle “Djamix,” and the email address djamix@mazafaka[.]ru.
From the forum’s inception until around 2008, Djamix was one of its most active and eloquent contributors. Djamix told forum members he was a lawyer, and nearly all of his posts included legal analyses of various public cases involving hackers arrested and charged with cybercrimes in Russia and abroad.
“Hiding with purely technical parameters will not help in a serious matter,” Djamix advised Maza members in September 2007. “In order to ESCAPE the law, you need to KNOW the law. This is the most important thing. Technical capabilities cannot overcome intelligence and cunning.”
Stalker himself credited Djamix with keeping Mazafaka online for so many years. In a retrospective post published to Livejournal in 2014 titled, “Mazafaka, from conception to the present day,” Stalker said Djamix had become a core member of the community.
“This guy is everywhere,” Stalker said of Djamix. “There’s not a thing on [Mazafaka] that he doesn’t take part in. For me, he is a stimulus-irritant and thanks to him, Maza is still alive. Our rallying force!”
Djamix told other forum denizens he was a licensed attorney who could be hired for remote or in-person consultations, and his posts on Mazafaka and other Russian boards show several hackers facing legal jeopardy likely took him up on this offer.
“I have the right to represent your interests in court,” Djamix said on the Russian-language cybercrime forum Verified in Jan. 2011. “Remotely (in the form of constant support and consultations), or in person – this is discussed separately. As well as the cost of my services.”
WHO IS DJAMIX?
A search on djamix@mazafaka[.]ru at DomainTools.com reveals this address has been used to register at least 10 domain names since 2008. Those include several websites about life in and around Sochi, Russia, the site of the 2014 Winter Olympics, as well as a nearby coastal town called Adler. All of those sites say they were registered to an Aleksei Safronov from Sochi who also lists Adler as a hometown.
The breach tracking service Constella Intelligence finds that the phone number associated with those domains — +7.9676442212 — is tied to a Facebook account for an Aleksei Valerievich Safronov from Sochi. Mr. Safronov’s Facebook profile, which was last updated in October 2022, says his ICQ instant messenger number is 53765. This is the same ICQ number assigned to Djamix in the Mazafaka user database.
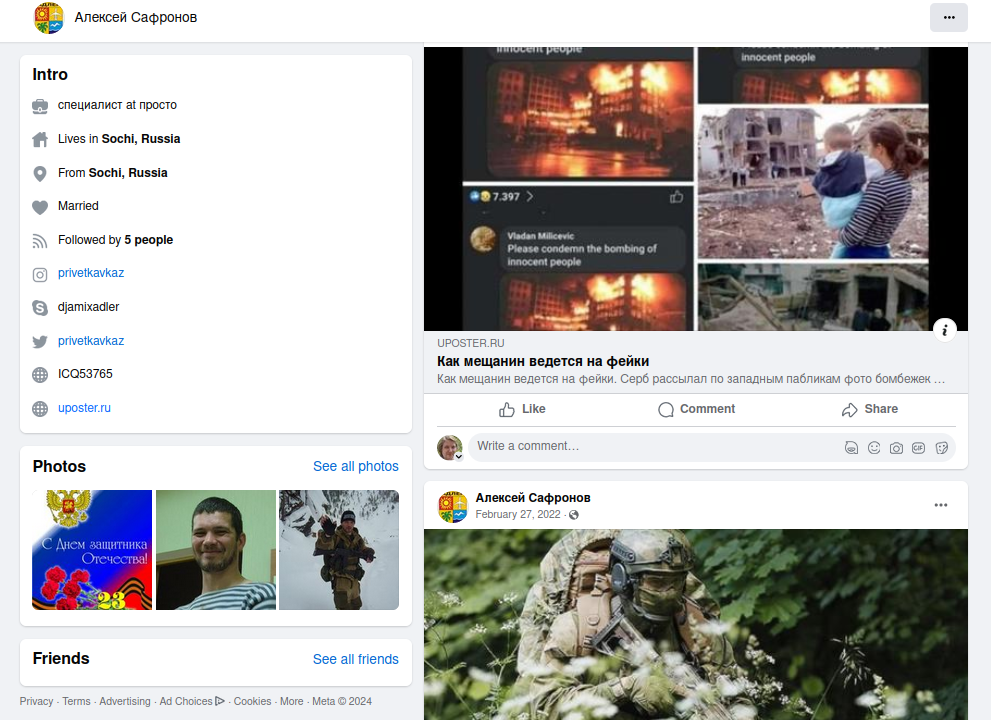
The Facebook account for Aleksey Safronov.
A “Djamix” account on the forum privetsochi[.]ru (“Hello Sochi”) says this user was born Oct. 2, 1970, and that his website is uposter[.]ru. This Russian language news site’s tagline is, “We Create Communication,” and it focuses heavily on news about Sochi, Adler, Russia and the war in Ukraine, with a strong pro-Kremlin bent.
Safronov’s Facebook profile also gives his Skype username as “Djamixadler,” and it includes dozens of photos of him dressed in military fatigues along with a regiment of soldiers deploying in fairly remote areas of Russia. Some of those photos date back to 2008.
In several of the images, we can see a patch on the arm of Safronov’s jacket that bears the logo of the Spetsnaz GRU, a special forces unit of the Russian military. According to a 2020 report from the Congressional Research Service, the GRU operates both as an intelligence agency — collecting human, cyber, and signals intelligence — and as a military organization responsible for battlefield reconnaissance and the operation of Russia’s Spetsnaz military commando units.

Mr. Safronov posted this image of himself on Facebook in 2016. The insignia of the GRU can be seen on his sleeve.
“In recent years, reports have linked the GRU to some of Russia’s most aggressive and public intelligence operations,” the CRS report explains. “Reportedly, the GRU played a key role in Russia’s occupation of Ukraine’s Crimea region and invasion of eastern Ukraine, the attempted assassination of former Russian intelligence officer Sergei Skripal in the United Kingdom, interference in the 2016 U.S. presidential elections, disinformation and propaganda operations, and some of the world’s most damaging cyberattacks.”
According to the Russia-focused investigative news outlet Meduza, in 2014 the Russian Defense Ministry created its “information-operation troops” for action in “cyber-confrontations with potential adversaries.”
“Later, sources in the Defense Ministry explained that these new troops were meant to ‘disrupt the potential adversary’s information networks,'” Meduza reported in 2018. “Recruiters reportedly went looking for ‘hackers who have had problems with the law.'”
Mr. Safronov did not respond to multiple requests for comment. A 2018 treatise written by Aleksei Valerievich Safronov titled “One Hundred Years of GRU Military Intelligence” explains the significance of the bat in the seal of the GRU.
“One way or another, the bat is an emblem that unites all active and retired intelligence officers; it is a symbol of unity and exclusivity,” Safronov wrote. “And, in general, it doesn’t matter who we’re talking about – a secret GRU agent somewhere in the army or a sniper in any of the special forces brigades. They all did and are doing one very important and responsible thing.”
It’s unclear what role Mr. Safronov plays or played in the GRU, but it seems likely the military intelligence agency would have exploited his considerable technical skills, knowledge and connections on the Russian cybercrime forums.
Searching on Safronov’s domain uposter[.]ru in Constella Intelligence reveals that this domain was used in 2022 to register an account at a popular Spanish-language discussion forum dedicated to helping applicants prepare for a career in the Guardia Civil, one of Spain’s two national police forces. Pivoting on that Russian IP in Constella shows three other accounts were created at the same Spanish user forum around the same date.
Mark Rasch, a former cybercrime prosecutor for the U.S. Department of Justice, said there has always been a close relationship between the GRU and the Russian hacker community. Rasch noted that in the early 2000s, the GRU was soliciting hackers with the skills necessary to hack US banks in order to procure funds to help finance Russia’s war in Chechnya.
“The guy is heavily hooked into the Russian cyber community, and that’s useful for intelligence services,” Rasch said. “He could have been infiltrating the community to monitor it for the GRU. Or he could just be a guy wearing a military uniform.”
from Krebs on Security https://krebsonsecurity.com/2024/02/from-cybercrime-saul-goodman-to-the-russian-gru/
Comments
Post a Comment