Krebs - Who’s Behind the Screencam Extortion Scam?
The sextortion email scam last month that invoked a real password used by each recipient and threatened to release embarrassing Webcam videos almost certainly was not the work of one criminal or even one group of criminals. Rather, it’s likely that additional spammers and scammers piled on with their own versions of the phishing email after noticing that some recipients were actually paying up. The truth is we may never find out who’s responsible, but it’s still fun to follow some promising early leads and see where they take us.

On Aug. 7, 2018 — five days before my story about the sextortion scam innovation went viral — a user on the forum of free email service hMailServer posted a copy of the sextortion email he received, noting that it included a password he’d formerly used online.
Helpfully, this user pasted a great deal of information from the spam email message, including the domain name from which it was sent (williehowell-dot-com) and the Internet address of the server that sent the message (46.161.42.91).
A look at the other domain names registered to this IP address block 46.161.42.x reveals some interesting patterns:
46.161.42.51 mail25.uscourtsgov[.]com
46.161.42.52 mail24.uscourtsgov[.]com
46.161.42.53 mail23.uscourtsgov[.]com
46.161.42.54 mail22.uscourtsgov[.]com
46.161.42.55 mail21.uscourtsgov[.]com
46.161.42.56 mail20.uscourtsgov[.]com
46.161.42.57 mail19.uscourtsgov[.]com
46.161.42.58 mail18.uscourtsgov[.]com
46.161.42.59 mail17.uscourtsgov[.]com
46.161.42.60 mail16.uscourtsgov[.]com
46.161.42.61 mail15.uscourtsgov[.]com
46.161.42.62 mail14.uscourtsgov[.]com
46.161.42.63 mail13.uscourtsgov[.]com
46.161.42.64 mail12.uscourtsgov[.]com
46.161.42.65 mail11.uscourtsgov[.]com
46.161.42.66 mail10.uscourtsgov[.]com
46.161.42.67 mail9.uscourtsgov[.]com
46.161.42.68 mail8.uscourtsgov[.]com
46.161.42.69 mail7.uscourtsgov[.]com
46.161.42.70 mail6.uscourtsgov[.]com
46.161.42.71 mail5.uscourtsgov[.]com
46.161.42.72 mail4.uscourtsgov[.]com
46.161.42.73 mail3.uscourtsgov[.]com
46.161.42.74 mail2.uscourtsgov[.]com
46.161.42.75 mail1.uscourtsgov[.]com
46.161.42.76 mail[.]commarysmith[.]com
46.161.42.77 mail.joancooper[.]com
46.161.42.78 mail.florencewoods[.]com
46.161.42.79 mail.ednawest[.]com
46.161.42.80 mail.ethelwebb[.]com
46.161.42.81 mail.eleanorhunt[.]com
46.161.42.82 mail.sallypierce[.]com
46.161.42.83 mail.reginaberry[.]com
46.161.42.84 mail.junecarroll[.]com
46.161.42.85 mail.robertaharper[.]com
46.161.42.86 mail.reneelane[.]com
46.161.42.87 mail.almaaustin[.]com
46.161.42.88 mail.elsiekelley[.]com
46.161.42.89 mail.vickifields[.]com
46.161.42.90 mail.ellaoliver[.]com
46.161.42.91 mail.williehowell[.]com
46.161.42.92 mail.veramccoy[.]com
46.161.42.93 mail.agnesbishop[.]com
46.161.42.94 mail.tanyagilbert[.]com
46.161.42.95 mail.mattiehoffman[.]com
46.161.42.96 mail.hildahopkins[.]com
46.161.42.97 beckymiles[.]com
46.161.42.98 mail.fayenorris[.]com
46.161.42.99 mail.joannaleonard[.]com
46.161.42.100 mail.rosieweber[.]com
46.161.42.101 mail.candicemanning[.]com
46.161.42.102 mail.sherirowe[.]com
46.161.42.103 mail.leticiagoodman[.]com
46.161.42.104 mail.myrafrancis[.]com
46.161.42.105 mail.jasminemaxwell[.]com
46.161.42.106 mail.eloisefrench[.]com
Search Google for any of those two-name domains above (e.g., fayenorris-dot-com) and you’ll see virtually all of them were used in these sextortion emails, and most were registered at the end of May 2018 through domain registrar Namecheap.
Notice the preponderance of the domain uscourtsgov-dot-com in the list above. All of those two-name domains used domain name servers (DNS servers) from uscourtsgov-dot-com at the time these emails were sent. In early June 2018, uscourtsgov-dot-com was associated with a Sigma ransomware scam delivered via spam. Victims who wanted their files back had to pay a bitcoin ransom.
In the months just before either the password-laced sextortion scam or the uscourtsgov-dot-com ransomware scam, uscourtsgov-com was devoid of content, aside from a message promoting the spamming services of the web site mtaexpert-dot-info. Uscourtsgov-dot-com is now offline, but it was active as of two weeks ago. Here’s what its homepage looked like:
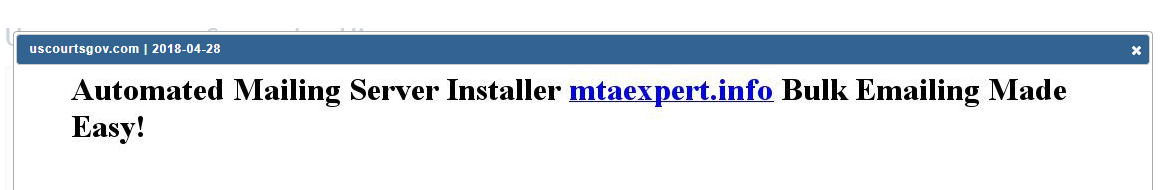
The domain uscourtsgov-dot-com was redirecting visitors to mtaexpert-dot-info for many months up to and including the sextortion email campaign. Image: Domaintools.com
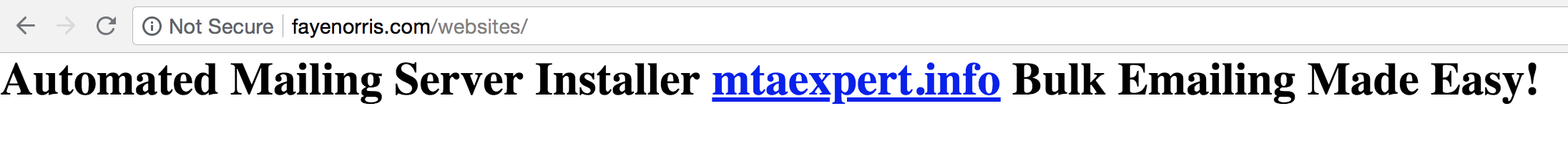
Interestingly, this same message promoting mtaexpert-dot-info appeared on the homepages of many other two-name domain names mentioned above (including fayenorris-dot-com):
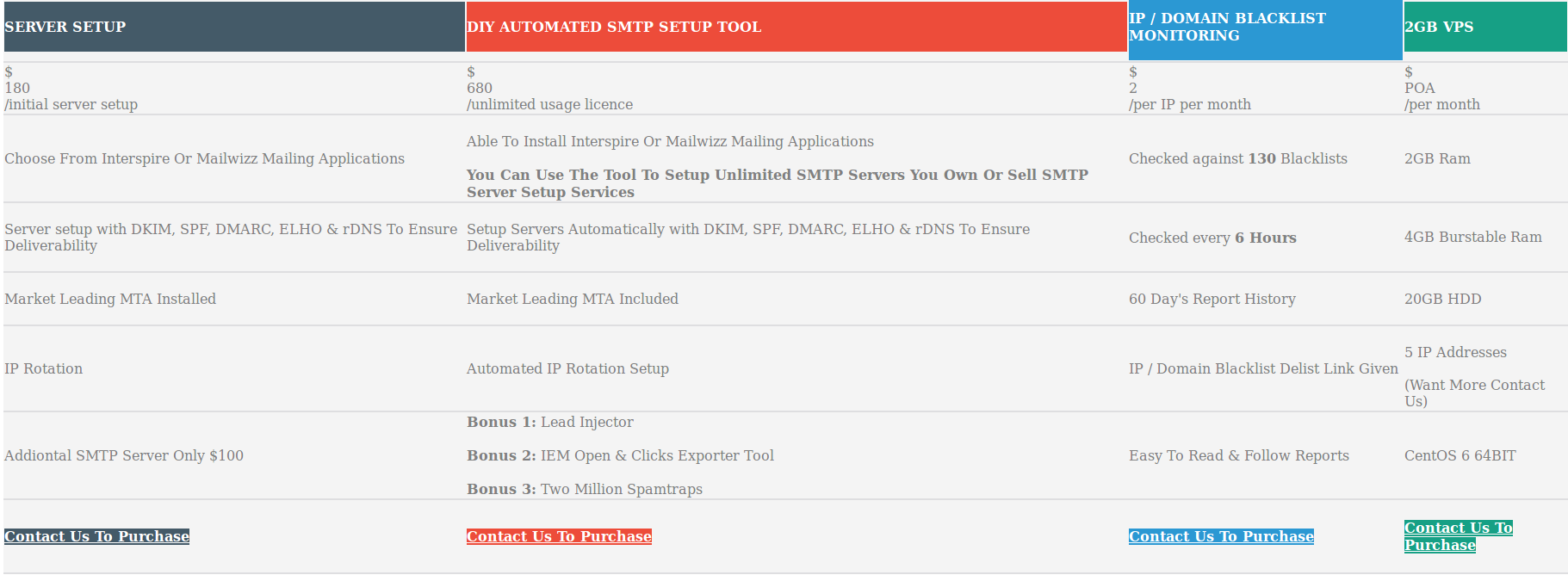
In the email delivery space, MTA stands for mail transfer agent, and this MTA Expert company is essentially an anonymous spamming service. The screen shot below is from an Internet Archive cached copy of mtaexpert-dot-info:
Mtaexpert-dot-info doesn’t disclose who owns the site, and current WHOIS registration records for the domain are obscured by privacy services. But thanks to a historic WHOIS record lookup at Domaintools.com [full disclosure: Domaintools is an advertiser on this site], we can see that for about a week in May 2018 the WHOIS privacy veil briefly dropped off and revealed the following record:
Registrant Name: HICHAM AALLAM
Registrant Organization: investissonsorg
Registrant Street: RED ANASS BLOC 26 N 3 ROUTE DE TETOUANE
Registrant City: TANGER
Registrant State/Province: Tanger-Tetouan
Registrant Postal Code: 90001
Registrant Country: MA
Registrant Phone: +212.626280317
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: hicham.aallam60@gmail.com
Who is Hicham Aallam? According to his LinkedIn page, he is an email marketer living in Morocco and working for a company called Active Sun Network. His resume says he also works for AdGenics, which according to anti-spam group Spamhaus is a well-known spamming operation with a long, sordid history. AdGenics, a.k.a. Cabo Networks a.k.a SIFT Logic, is currently Number Six on Spamhaus’ Top Ten Worst Spammers list.
Contacted via LinkedIn, Aallam said he was unaware that his email service was used in the either the sextortion or ransomware campaigns linked to the above-mentioned domains. He said an ad for Mtaexpert-dot-info automatically gets shown on the home page of any site that is configured to use his email-sending scripts.
Aallam says he charges customers to use these scripts, but that he only had one semi-recent customer: A person who contacted him using the Skype name “brian.ortega_4” paid roughly $250 worth of the cryptocurrency Ethereum (ETH) on Apr. 3, 2018 for a license to MTA Experts’ mailing script. Here is a record of that transaction. All of the ETH transactions attributed to and from that account can be seen here.
Okay, so we still might not know who’s responsible for sending some of these sextortion emails, and it could well be one of Aallam’s other clients behind these two schemes. Nevertheless, it’s always fascinating to see how far one can get just by following a few breadcrumbs.
One final breadcrumb to follow: The Internet address space occupied by the uscourtsgov-dot-com and the sextortion-related domains — 46.161.42.0/24. In May 2018, RiskIQ published a detailed report (PDF) about a complex phishing scheme that used an address adjacent to uscourtsgov-dot-com in a bid to steal Ethereum from MyEtherWallet users.
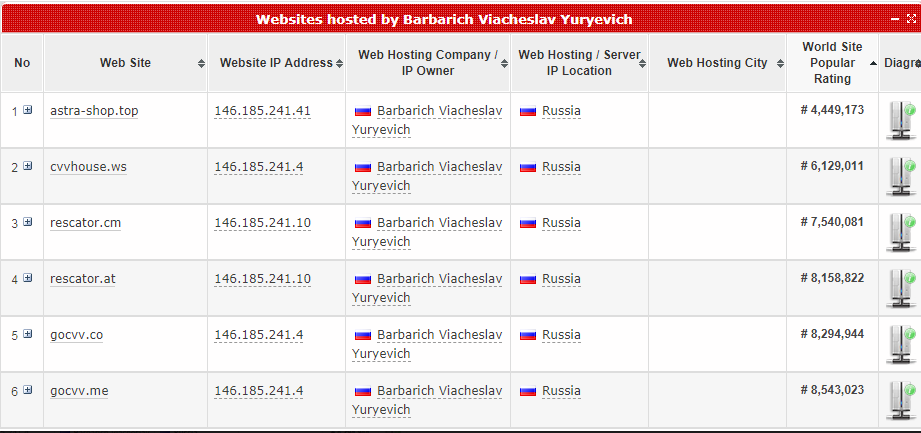
The registered owner of the Internet address space is a “Barbarich_Viacheslav_Yuryevich,” which is the same name as the owner of the network AS41995, a.k.a. web-shield-dot-biz. 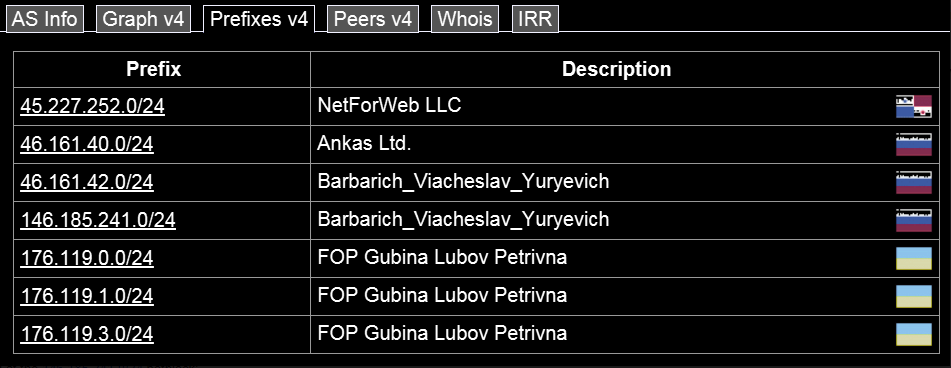
A different block of addresses that we can see in the graphic above assigned to Web-Shield — 146.185.241.0/24 — contains a metric truckload of domains involved in selling stolen credit cards.
Loyal readers of this site will notice a familiar domain there: Rescator. It belongs to a seasonsed cybercriminal by the same name who has been closely linked to the Target and Sally Beauty breaches, among many others. To this day — almost four years after the Target breach — the home page to Rescator’s stolen card shop includes a picture of Yours Truly as a postage stamp that reads, “As advertised by Brian Krebs.”
KrebsOnSecurity would like to thank security researcher Troy Mursch and anti-spam crusader Ron Guilmette for their assistance in this research.
from Krebs on Security https://krebsonsecurity.com/2018/08/whos-behind-the-screencam-extortion-scam/

Comments
Post a Comment