Krebs - 773M Password ‘Megabreach’ is Years Old
My inbox and Twitter messages positively lit up today with people forwarding stories from Wired and other publications about a supposedly new trove of nearly 773 million unique email addresses and 21 million unique passwords that were posted to a hacking forum. A story in The Guardian breathlessly dubbed it “the largest collection ever of breached data found.” But in an interview with the apparent seller, KrebsOnSecurity learned that it is not even close to the largest gathering of stolen data, and that it is at least two to three years old.
The dump, labeled “Collection #1” and approximately 87GB in size, was first detailed earlier today by Troy Hunt, who operates the HaveIBeenPwned breach notification service. Hunt said the data cache was likely “made up of many different individual data breaches from literally thousands of different sources.”
KrebsOnSecurity sought perspective on this discovery from Alex Holden, CTO of Hold Security, a company that specializes in trawling underground spaces for intelligence about malicious actors and their stolen data dumps. Holden said the data appears to have first been posted to underground forums in October 2018, and that it is just a subset of a much larger tranche of passwords being peddled by a shadowy seller online.
Here’s a screenshot of a subset of that seller’s current offerings, which total almost 1 Terabyte of stolen and hacked passwords:
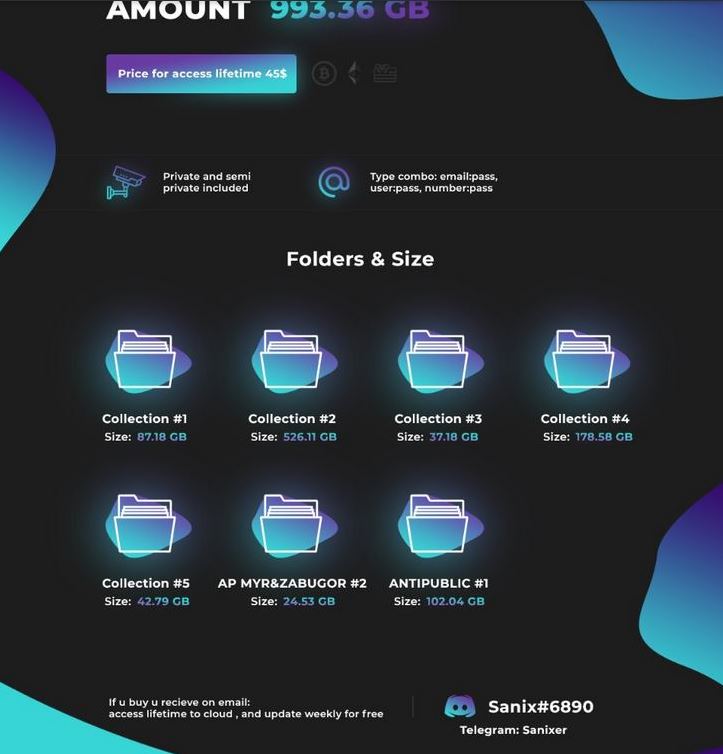
The 87GB “Collection1” archive is one of but many similar tranches of stolen passwords being sold by a particularly prolific ne’er-do-well in the underground.
As we can see above, Collection #1 offered by this seller is indeed 87GB in size. He also advertises a Telegram username where he can be reached — “Sanixer.” So, naturally, KrebsOnSecurity contacted Sanixer via Telegram to find out more about the origins of Collection #1, which he is presently selling for the bargain price of just $45.
Sanixer said Collection#1 consists of data pulled from a huge number of hacked sites, and was not exactly his “freshest” offering. Rather, he sort of steered me away from that archive, suggested that — unlike most of his other wares — Collection #1 was at least 2-3 years old. His other password packages, which he said are not all pictured in the above screen shot and total more than 4 terabytes in size, are less than a year old, Sanixer explained.
By way of explaining the provenance of Collection #1, Sanixer said it was a mix of “dumps and leaked bases,” and then he offered an interesting screen shot of his additional collections. Click on the image below and notice the open Web browser tab behind his purloined password trove (which is apparently stored at Mega.nz): Troy Hunt’s published research on this 773 million Collection #1.

Sanixer says Collection #1 was from a mix of sources. A description of those sources can be seen in the directory tree on the left side of this screenshot.
Holden said the habit of collecting large amounts of credentials and posting it online is not new at all, and that the data is far more useful for things like phishing, blackmail and other indirect attacks — as opposed to plundering inboxes. Holden added that his company had already derived 99 percent of the data in Collection #1 from other sources.
“It was popularized several years ago by Russian hackers on various Dark Web forums,” he said. “Because the data is gathered from a number of breaches, typically older data, it does not present a direct danger to the general user community. Its sheer volume is impressive, yet, by account of many hackers the data is not greatly useful.”
A core reason so many accounts get compromised is that far too many people have the nasty habit(s) of choosing poor passwords, re-using passwords and email addresses across multiple sites, and not taking advantage of multi-factor authentication options when they are available.
If this Collection #1 has you spooked, changing your password(s) certainly can’t hurt — unless of course you’re in the habit of re-using passwords. Please don’t do that. As we can see from the offering above, your password is probably worth way more to you than it is to cybercriminals (in the case of Collection #1, just .000002 cents per password).
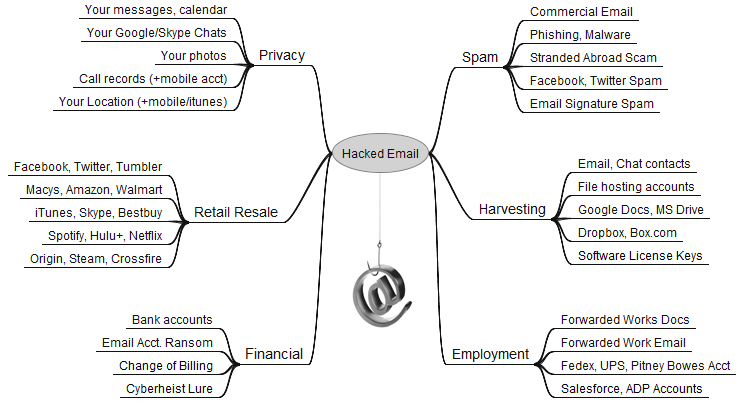
For most of us, by far the most important passwords are those protecting our email inbox(es). That’s because in nearly all cases, the person who is in control of that email address can reset the password of any services or accounts tied to that email address – merely by requesting a password reset link via email. For more on this dynamic, please see The Value of a Hacked Email Account.
And instead of thinking about passwords, consider using unique, lengthy passphrases — collections of words in an order you can remember — when a site allows it. In general, a long, unique passphrase takes for more effort to crack than a short, complex one. Unfortunately, many sites do not let users choose passwords or passphrases that exceed a small number of characters, or they will otherwise allow long passphrases but ignore anything entered after the character limit is reached.
If you are the type of person who likes to re-use passwords, then you definitely need to be using a password manager, which helps you pick and remember strong and unique passwords/passphrases and essentially lets you use the same strong master password/passphrase across all Web sites.
Finally, if you haven’t done so lately, mosey on over to twofactorauth.org and see if you are taking full advantage of multi-factor authentication at sites you trust with your data. The beauty of multi-factor is that even if thieves manage to guess or steal your password just because they hacked some Web site, that password will be useless to them unless they can also compromise that second factor — be it your mobile device or security key.
from Krebs on Security https://krebsonsecurity.com/2019/01/773m-password-megabreach-is-years-old/
Comments
Post a Comment