Krebs - Interview With the Guy Who Tried to Frame Me for Heroin Possession
In April 2013, I received via U.S. mail more than a gram of pure heroin as part of a scheme to get me arrested for drug possession. But the plan failed and the Ukrainian mastermind behind it soon after was imprisoned for unrelated cybercrime offenses. That individual recently gave his first interview since finishing his jail time here in the states, and he’s shared some select (if often abrasive and coarse) details on how he got into cybercrime and why. Below are a few translated excerpts.
When I first encountered now-31-year-old Sergei “Fly,” “Flycracker,” “MUXACC” Vovnenko in 2013, he was the administrator of the fraud forum “thecc[dot]bz,” an exclusive and closely guarded Russian language board dedicated to financial fraud and identity theft.
Many of the heavy-hitters from other fraud forums had a presence on Fly’s forum, and collectively the group financed and ran a soup-to-nuts network for turning hacked credit card data into mounds of cash.
Vovnenko first came onto my radar after his alter ego Fly published a blog entry that led with an image of my bloodied, severed head and included my credit report, copies of identification documents, pictures of our front door, information about family members, and so on. Fly had invited all of his cybercriminal friends to ruin my financial identity and that of my family.
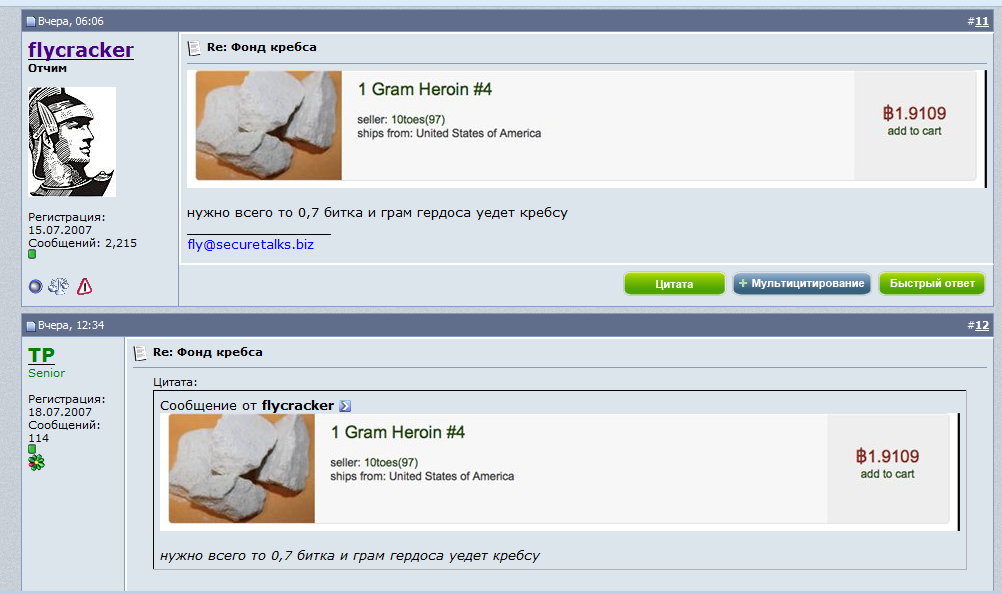
Somewhat curious about what might have precipitated this outburst, I was secretly given access to Fly’s cybercrime forum and learned he’d freshly hatched a plot to have heroin sent to my home. The plan was to have one of his forum lackeys spoof a call from one of my neighbors to the police when the drugs arrived, complaining that drugs were being delivered to our house and being sold out of our home by Yours Truly.
Thankfully, someone on Fly’s forum also posted a link to the tracking number for the drug shipment. Before the smack arrived, I had a police officer come out and take a report. After the heroin showed up, I gave the drugs to the local police and wrote about the experience in Mail From the Velvet Cybercrime Underground.
Angry that I’d foiled the plan to have me arrested for being a smack dealer, Fly or someone on his forum had a local florist send a gaudy floral arrangement in the shape of a giant cross to my home, complete with a menacing message that addressed my wife and was signed, “Velvet Crabs.”

The floral arrangement that Fly or one of his forum lackeys had delivered to my home in Virginia.
Vovnenko was arrested in Italy in the summer of 2014 on identity theft and botnet charges, and spent some 15 months in arguably Italy’s worst prison contesting his extradition to the United States. Those efforts failed, and he soon pleaded guilty to aggravated identity theft and wire fraud, and spent several years bouncing around America’s prison system.
Although Vovnenko sent me a total of three letters from prison in Naples (a hand-written apology letter and two friendly postcards), he never responded to my requests to meet him following his trial and conviction on cybercrime charges in the United States. I suppose that is fair: To my everlasting dismay, I never responded to his Italian dispatches (the first I asked to be professionally analyzed and translated before I would touch it).

Seasons greetings from my pen pal, Flycracker.
After serving his 41 month sentence in the U.S., Vovnenko was deported, although it’s unclear where he currently resides (the interview excerpted here suggests he’s back in Italy, but Fly doesn’t exactly confirm that).
In an interview published on the Russian-language security blog Krober[.]biz, Vovnenko said he began stealing early in life, and by 13 was already getting picked up for petty robberies and thefts.
A translated English version of the interview was produced and shared with KrebsOnSecurity by analysts at New York City-based cyber intelligence firm Flashpoint.
Sometime in the mid-aughts, Vovnenko settled with his mother in Naples, Italy, but he had trouble keeping a job for more than a few days. Until a chance encounter led to a front job at a den of thieves.
“When I came to my Mom in Naples, I could not find a permanent job. Having settled down somewhere at a new job, I would either get kicked out or leave in the first two days. I somehow didn’t succeed with employment until I was invited to work in a wine shop in the historical center of Naples, where I kinda had to wipe the dust from the bottles. But in fact, the wine shop turned out to be a real den and a sales outlet of hashish and crack. So my job was to be on the lookout and whenever the cops showed up, take a bag of goods and leave under the guise of a tourist.”
Cocaine and hash were plentiful at his employer’s place of work, and Vovnenko said he availed himself of both abundantly. After he’d saved enough to buy a computer, Fly started teaching himself how to write programs and hack stuff. He quickly became enthralled with the romanticized side of cybercrime — the allure of instant cash — and decided this was his true vocation.
“After watching movies and reading books about hackers, I really wanted to become a sort of virtual bandit who robs banks without leaving home,” Vovnenko recalled. “Once, out of curiosity, I wrote an SMS bomber that used a registration form on a dating site, bypassing the captcha through some kind of rookie mistake in the shitty code. The bomber would launch from the terminal and was written in Perl, and upon completion of its work, it gave out my phone number and email. I shared the bomber somewhere on one of my many awkward sites.”
“And a couple of weeks later they called me. Nah, not the cops, but some guy who comes from Sri Lanka who called himself Enrico. He told me that he used my program and earned a lot of money, and now he wants to share some of it with me and hire me. By a happy coincidence, the guy also lived in Naples.”
“When we met in person, he told me that he used my bomber to fuck with a telephone company called Wind. This telephone company had such a bonus service: for each incoming SMS you received two cents on the balance. Well, of course, this guy bought a bunch of SIM cards and began to bomb them, getting credits and loading them into his paid lines, similar to how phone sex works.”
But his job soon interfered with his drug habit, and he was let go.
“At the meeting, Enrico gave me 2K euros, and this was the first money I’ve earned, as it is fashionable to say these days, on ‘cybercrime’. I left my previous job and began to work closely with Enrico. But always stoned out of my mind, I didn’t do a good job and struggled with drug addiction at that time. I was addicted to cocaine, as a result, I was pulling a lot more money out of Enrico than my work brought him. And he kicked me out.”
After striking out on his own, Vovnenko says he began getting into carding big time, and was introduced to several other big players on the scene. One of those was a cigarette smuggler who used the nickname Ponchik (“Doughnut”).
I wonder if this is the same Ponchik who was arrested in 2013 as being the mastermind behind the Blackhole exploit kit, a crimeware package that fueled an overnight explosion in malware attacks via Web browser vulnerabilities.
In any case, Vovnenko had settled on some schemes that were generating reliably large amounts of cash.
“I’ve never stood still and was not focusing on carding only, with the money I earned, I started buying dumps and testing them at friends’ stores,” Vovnenko said. “Mules, to whom I signed the hotlines, were also signed up for cashing out the loads, giving them a mere 10 percent for their work. Things seemed to be going well.”
FAN MAIL
There is a large chronological gap in Vovnenko’s account of his cybercrime life story from that point on until the time he and his forum friends started sending heroin, large bags of feces and other nasty stuff to our Northern Virginia home in 2013.
Vovnenko claims he never sent anything and that it was all done by members of his forum.
-Tell me about the packages to Krebs.
“That ain’t me. Suitcase filled with sketchy money, dildoes, and a bouquet of coffin wildflowers. They sent all sorts of crazy shit. Forty or so guys would send. When I was already doing time, one of the dudes sent it. By the way, Krebs wanted to see me. But the lawyer suggested this was a bad idea. Maybe he wanted to look into my eyes.”
In one part of the interview, Fly is asked about but only briefly touches on how he was caught. I wanted to add some context here because this part of the story is richly ironic, and perhaps a tad cathartic.
Around the same time Fly was taking bitcoin donations for a fund to purchase heroin on my behalf, he was also engaged to be married to a nice young woman. But Fly apparently did not fully trust his bride-to-be, so he had malware installed on her system that forwarded him copies of all email that she sent and received.
But Fly would make at least two big operational security mistakes in this spying effort: First, he had his fiancée’s messages forwarded to an email account he’d used for plenty of cybercriminal stuff related to his various “Fly” identities.
Mistake number two was the password for his email account was the same as one of his cybercrime forum admin accounts. And unbeknownst to him at the time, that forum was hacked, with all email addresses and hashed passwords exposed.
Soon enough, investigators were reading Fly’s email, including the messages forwarded from his wife’s account that had details about their upcoming nuptials, such as shipping addresses for their wedding-related items and the full name of Fly’s fiancée. It didn’t take long to zero in on Fly’s location in Naples.
While it may sound unlikely that a guy so immeshed in the cybercrime space could make such rookie security mistakes, I have found that a great many cybercriminals actually have worse operational security than the average Internet user.
I suspect this may be because the nature of their activities requires them to create vast numbers of single- or brief-use accounts, and in general they tend to re-use credentials across multiple sites, or else pick very poor passwords — even for critical resources.
In addition to elaborating on his hacking career, Fly talks a great deal about his time in various prisons (including their culinary habits), and an apparent longing or at least lingering fondness for the whole carding scene in general.
Towards the end, Fly says he’s considering going back to school, and that he may even take up information security as a study. I wish him luck in that whatever that endeavor is as long as he can also avoid stealing from people.
I don’t know what I would have written many years ago to Fly had I not been already so traumatized by receiving postal mail from him. Perhaps it would go something like this:
“Dear Fly: Thank you for your letters. I am very sorry to hear about the delays in your travel plans. I wish you luck in all your endeavors — and I sincerely wish the next hopeful opportunity you alight upon does not turn out to be a pile of shit.”
The entire translated interview is here (PDF). Fair warning: Many readers may find some of the language and topics discussed in the interview disturbing or offensive.
from Krebs on Security https://krebsonsecurity.com/2019/09/interview-with-the-guy-who-tried-to-frame-me-for-heroin-possession/
Comments
Post a Comment