Krebs - US Government Sites Give Bad Security Advice
Many U.S. government Web sites now carry a message prominently at the top of their home pages meant to help visitors better distinguish between official U.S. government properties and phishing pages. Unfortunately, part of that message is misleading and may help perpetuate a popular misunderstanding about Web site security and trust that phishers have been exploiting for years now.
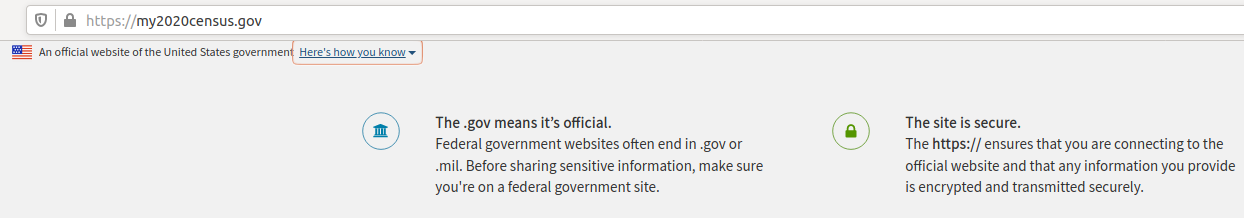
For example, the official U.S. Census Bureau website https://my2020census.gov carries a message that reads, “An official Web site of the United States government. Here’s how you know.” Clicking the last part of that statement brings up a panel with the following information:
The text I have a beef with is the bit on the right, beneath the “This site is secure” statement. Specifically, it says, “The https:// ensures that you are connecting to the official website….”
Here’s the deal: The https:// part of an address (also called “Secure Sockets Layer” or SSL) merely signifies the data being transmitted back and forth between your browser and the site is encrypted and cannot be read by third parties.
However, the presence of “https://” or a padlock in the browser address bar does not mean the site is legitimate, nor is it any proof the site has been security-hardened against intrusion from hackers.
In other words, while readers should never transmit sensitive information to a site that does not use https://, the presence of this security feature tells you nothing about the trustworthiness of the site in question.
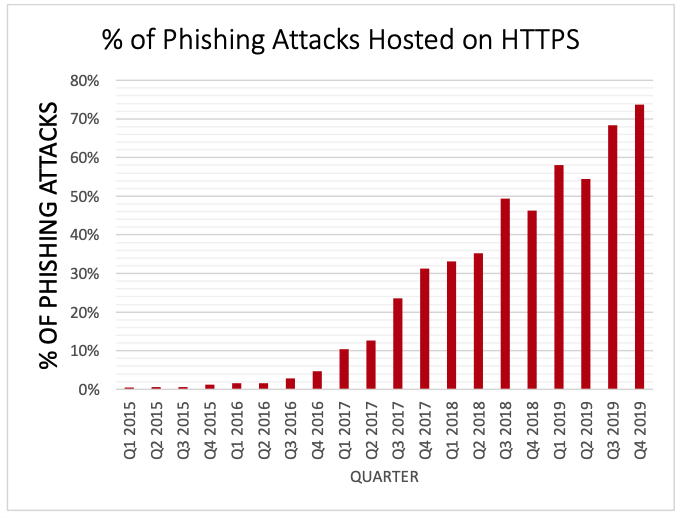
Here’s a sobering statistic: According to PhishLabs, by the end of 2019 roughly three-quarters (74 percent) of all phishing sites were using SSL certificates. PhishLabs found this percentage increased from 68% in Q3 and 54% in Q2 of 2019.
“Attackers are using free certificates on phishing sites that they create, and are abusing the encryption already installed on hacked web sites,” PhishLabs founder and CTO John LaCour said.
The truth is anyone can get an SSL certificate for free, and that’s a big reason why most phishing sites now have them. The other reason is that they help phishers better disguise their sites as legitimate, since many Web browsers now throw up security warnings on non-https:// sites.
KrebsOnSecurity couldn’t find any reliable information on how difficult it may be to obtain an SSL certificate for a .gov site once one has a .gov domain, but it is apparently not difficult for just about anyone to get their very own .gov domain name.
The U.S. General Services Administration (GSA), which oversees the issuance of .gov domains, recently made it a tiny bit more difficult to do so — by requiring all applications be notarized — but this seems a small hurdle for scam artists to clear.
Regardless, it seems the federal government is doing consumers a disservice with this messaging, by perpetuating the myth that the presence of “https://” in a link denotes any kind of legitimacy.
“‘Https’ does not mean that you are at the correct website or that the site is secure,” LaCour said. “It only indicates that the connection is encrypted. The server could still be misconfigured or have software vulnerabilities. It is good that they mention to look for ‘.gov’. There’s no guarantee that a .gov website is secure, but it should help ensure that visitors are on the right website.”
I should note that this misleading message seems to be present only on some federal government Web sites. For instance, while the sites for the GSA, the Department of Labor, Department of Transportation, and Department of Veterans Affairs all include the same wording, those for the Commerce Department and Justice Department are devoid of the misleading text, stating:
“This site is also protected by an SSL (Secure Sockets Layer) certificate that’s been signed by the U.S. government. The https:// means all transmitted data is encrypted — in other words, any information or browsing history that you provide is transmitted securely.”
Other federal sites — like dhs.gov, irs.gov and epa.gov — simply have the “An official website of the United States government” declaration at the top, without offering any tips about how to feel better about that statement.
from Krebs on Security https://krebsonsecurity.com/2020/03/us-government-sites-give-bad-security-advice/
Comments
Post a Comment