Krebs - How Cybercriminals are Weathering COVID-19
In many ways, the COVID-19 pandemic has been a boon to cybercriminals: With unprecedented numbers of people working from home and anxious for news about the virus outbreak, it’s hard to imagine a more target-rich environment for phishers, scammers and malware purveyors. In addition, many crooks are finding the outbreak has helped them better market their cybercriminal wares and services. But it’s not all good news: The Coronavirus also has driven up costs and disrupted key supply lines for many cybercriminals. Here’s a look at how they’re adjusting to these new realities.
FUELED BY MULES
One of the more common and perennial cybercriminal schemes is “reshipping fraud,” wherein crooks buy pricey consumer goods online using stolen credit card data and then enlist others to help them collect or resell the merchandise.
Most online retailers years ago stopped shipping to regions of the world most frequently associated with credit card fraud, including Eastern Europe, North Africa, and Russia. These restrictions have created a burgeoning underground market for reshipping scams, which rely on willing or unwitting residents in the United States and Europe — derisively referred to as “reshipping mules” — to receive and relay high-dollar stolen goods to crooks living in the embargoed areas.
But apparently a number of criminal reshipping services are reporting difficulties due to the increased wait time when calling FedEx or UPS (to divert carded goods that merchants end up shipping to the cardholder’s address instead of to the mule’s). In response, these operations are raising their prices and warning of longer shipping times, which in turn could hamper the activities of other actors who depend on those services.
That’s according to Intel 471, a cyber intelligence company that closely monitors hundreds of online crime forums. In a report published today, the company said since late March 2020 it has observed several crooks complaining about COVID-19 interfering with the daily activities of their various money mules (people hired to help launder the proceeds of cybercrime).
“One Russian-speaking actor running a fraud network complained about their subordinates (“money mules”) in Italy, Spain and other countries being unable to withdraw funds, since they currently were afraid to leave their homes,” Intel 471 observed. “Also some actors have reported that banks’ customer-support lines are being overloaded, making it difficult for fraudsters to call them for social-engineering activities (such as changing account ownership, raising withdrawal limits, etc).”
Still, every dark cloud has a silver lining: Intel 471 noted many cybercriminals appear optimistic that the impending global economic recession (and resultant unemployment) “will make it easier to recruit low-level accomplices such as money mules.”
Alex Holden, founder and CTO of Hold Security, agreed. He said while the Coronavirus has forced reshipping operators to make painful shifts in several parts of their business, the overall market for available mules has never looked brighter.
“Reshipping is way up right now, but there are some complications,” he said.
For example, reshipping scams have over the years become easier for both reshipping mule operators and the mules themselves. Many reshipping mules are understandably concerned about receiving stolen goods at their home and risking a visit from the local police. But increasingly, mules have been instructed to retrieve carded items from third-party locations.
“The mules don’t have to receive stolen goods directly at home anymore,” Holden said. “They can pick them up at Walgreens, Hotel lobbies, etc. There are a ton of reshipment tricks out there.”
But many of those tricks got broken with the emergence of COVID-19 and social distancing norms. In response, more mule recruiters are asking their hires to do things like reselling goods shipped to their homes on platforms like eBay and Amazon.
“Reshipping definitely has become more complicated,” Holden said. “Not every mule will run 10 times a day to the post office, and some will let the goods sit by the mailbox for days. But on the whole, mules are more compliant these days.”
GIVE AND TAKE
KrebsOnSecurity recently came to a similar conclusion: Last month’s story, “Coronavirus Widens the Money Mule Pool,” looked at one money mule operation that had ensnared dozens of mules with phony job offers in a very short period of time. Incidentally, the fake charity behind that scheme — which promised to raise money for Coronavirus victims — has since closed up shop and apparently re-branded itself as the Tessaris Foundation.
Charitable cybercriminal endeavors were the subject of a report released this week by cyber intel firm Digital Shadows, which looked at various ways computer crooks are promoting themselves and their hacking services using COVID-19 themed discounts and giveaways.
Like many commercials on television these days, such offers obliquely or directly reference the economic hardships wrought by the virus outbreak as a way of connecting on an emotional level with potential customers.
“The illusion of philanthropy recedes further when you consider the benefits to the threat actors giving away goods and services,” the report notes. “These donors receive a massive boost to their reputation on the forum. In the future, they may be perceived as individuals willing to contribute to forum life, and the giveaways help establish a track record of credibility.”
Brian’s Club — one of the underground’s largest bazaars for selling stolen credit card data and one that has misappropriated this author’s likeness and name in its advertising — recently began offering “pandemic support” in the form of discounts for its most loyal customers.

It stands to reason that the virus outbreak might depress cybercriminal demand for “dumps,” or stolen account data that can be used to create physical counterfeit credit cards. After all, dumps are mainly used to buy high-priced items from electronics stores and other outlets that may not even be open now thanks to the widespread closures from the pandemic.
If that were the case, we’d also expect to see dumps prices fall significantly across the cybercrime economy. But so far, those price changes simply haven’t materialized, says Gemini Advisory, a New York based company that monitors the sale of stolen credit card data across dozens of stores in the cybercrime underground.
Stas Alforov, Gemini’s director of research and development, said there’s been no notable dramatic changes in pricing for both dumps and card data stolen from online merchants (a.k.a. “CVVs”) — even though many cybercrime groups appear to be massively shifting their operations toward targeting online merchants and their customers.
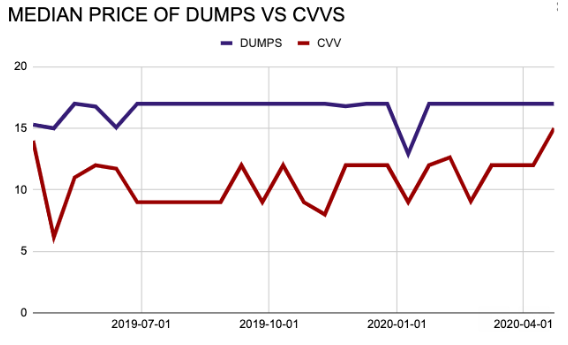
“Usually, the huge spikes upward or downward during a short period is reflected by a large addition of cheap records that drive the median price change,” Alforov said, referring to the small and temporary price deviations depicted in the graph above.
Intel 471 said it came to a similar conclusion.
“You might have thought carding activity, to include support aspects such as checker services, would decrease due to both the global lockdown and threat actors being infected with COVID-19,” the company said. “We’ve even seen some actors suggest as much across some shops, but the reality is there have been no observations of major changes.”
CONSCIENCE VS. COMMERCE
Interestingly, the Coronavirus appears to have prompted discussion on a topic that seldom comes up in cybercrime communities — i.e., the moral and ethical ramifications of their work. Specifically, there seems to be much talk these days about the potential karmic consequences of cashing in on the misery wrought by a global pandemic.
For example, Digital Shadows said some have started to question the morality of targeting healthcare providers, or collecting funds in the name of Coronavirus causes and then pocketing the money.
“One post on the gated Russian-language cybercriminal forum Korovka laid bare the question of threat actors’ moral obligation,” the company wrote. “A user initiated a thread to canvass opinion on the feasibility of faking a charitable cause and collecting donations. They added that while they recognized that such a plan was ‘cruel,’ they found themselves in an ‘extremely difficult financial situation.’ Responses to the proposal were mixed, with one forum user calling the plan ‘amoral,’ and another pointing out that cybercrime is inherently an immoral affair.”
from Krebs on Security https://krebsonsecurity.com/2020/04/how-cybercriminals-are-weathering-covid-19/
Comments
Post a Comment