Krebs - Sipping from the Coronavirus Domain Firehose
Security experts are poring over thousands of new Coronavirus-themed domain names registered each day, but this often manual effort struggles to keep pace with the flood of domains invoking the virus to promote malware and phishing sites, as well as non-existent healthcare products and charities. As a result, domain name registrars are under increasing pressure to do more to combat scams and misinformation during the COVID-19 pandemic.
By most measures, the volume of new domain registrations that include the words “Coronavirus” or “Covid” has closely tracked the spread of the deadly virus. The Cyber Threat Coalition (CTC), a group of several thousand security experts volunteering their time to fight COVID-related criminal activity online, recently published data showing the rapid rise in new domains began in the last week of February, around the same time the Centers for Disease Control began publicly warning that a severe global pandemic was probably inevitable.
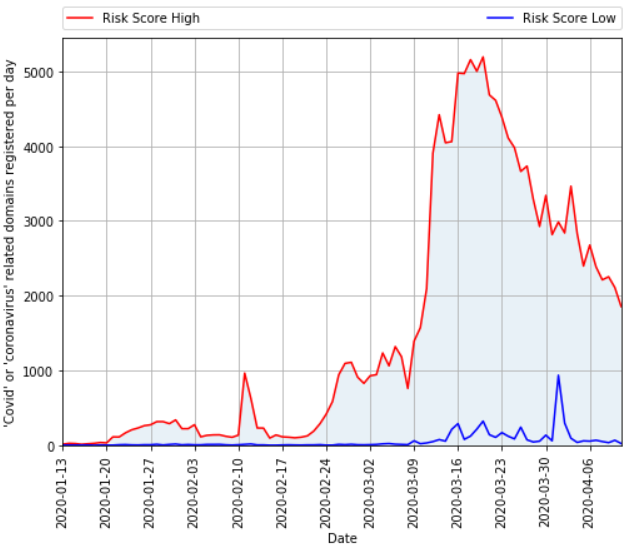
The total number of domains registered per day that contain a COVID-19 related term, according to DomainTools. The red line indicates the count of domains that DomainTools determined are “likely malicious.” The blue line refers to domains that are likely benign.
“Since March 20th, the number of risky domains registered per day has been decreasing, with a notable spike around March 30th,” wrote John Conwell, principal data scientist at DomainTools [an advertiser on this site]. “Interestingly, legitimate organizations creating domains in response to the COVID-19 crisis were several weeks behind the curve from threat actors trying to take advantage of this situation. This is a pattern DomainTools hasn’t seen before in other crises.”
Security vendor Sophos looked at telemetry from customer endpoints to illustrate the number of new COVID-related domains that actually received traffic of late. As the company noted, one challenge in identifying potentially malicious domains is that many of them can sit dormant for days or weeks before being used for anything.
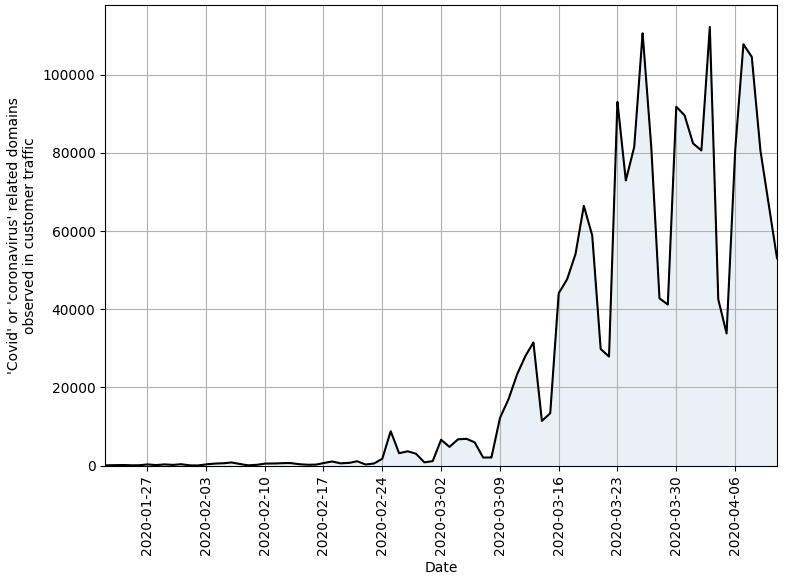
Data from security vendor Sophos, published by the Cyber Threat Coalition, shows the number of Coronavirus or COVID-19 themed domains registered per week that received traffic.
“We can see a rapid and dramatic increase of visits to potentially malicious domains exploiting the Coronavirus pandemic week over week, beginning in late February,” wrote Sophos’ Rich Harang. “Even though still a minority of cyber threats use the pandemic as a lure, some of these new domains will eventually be used for malicious purposes.”
CTC spokesman Nick Espinosa said the first spike in visits was on February 25, when group members saw about 4,000 visits to the sites they were tracking.
“The following two weeks starting on March 9 saw rapid growth, and from March 23 onwards we’re seeing between 75,000 to 130,000 visits per weekday, and about 40,000 on the weekends,” Espinosa said. “Looking at the data collected, the pattern of visits are highest on Monday and Friday, and the lowest visit count is on the weekend. Our data shows that there were virtually no customer hits on COVID-related domains prior to February 23.”
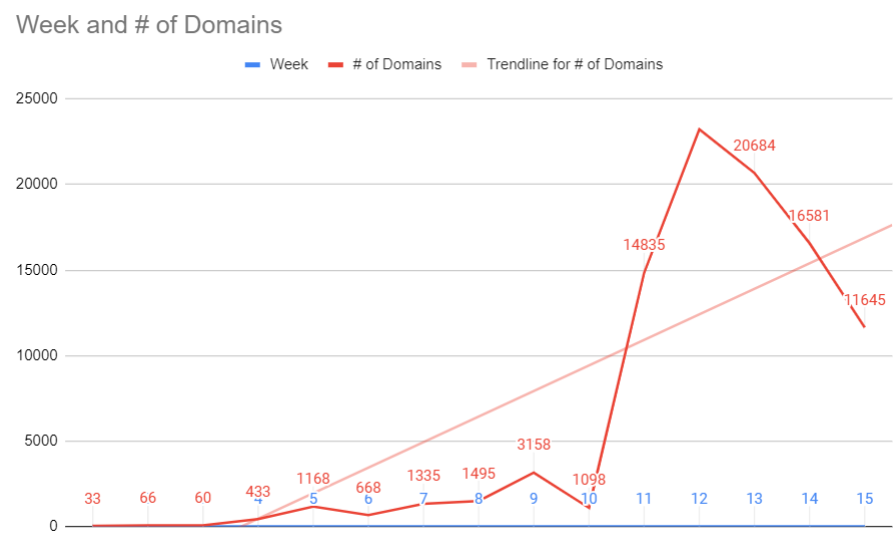
Milwaukee-based Hold Security has been publishing daily and weekly lists of all COVID-19 related domain registrations (without any scoring assigned). Here’s a graph KrebsOnSecurity put together based on that data set, which also shows a massive spike in new domain registrations in the third week of March, trailing off considerably over the past couple of weeks.
Not everyone is convinced we’re measuring the right things, or that the current measurements are accurate. Neil Schwartzman, executive director of the anti-spam group CAUCE, said he believes DomainTool’s estimates on the percentage of new COVID/Coronavirus-themed domains that are malicious are too high, and that many are likely benign and registered by well-meaning people seeking to share news or their own thoughts about the outbreak.
“But there’s the rub,” he said. “Bad guys get to hide amidst the good really effectively, so each one needs to be reviewed on its own. And that’s a substantial amount of work.”
At the same time, Schwartzman said, focusing purely on domains may obscure the true size and scope of the overall threat. That’s because scammers very often will establish multiple subdomains for each domain, meaning that a single COVID-related new domain registration could eventually be tied to a number of different scammy or malicious sites.
Subdomains can not only make phishing domains appear more legitimate, but they also tend to lengthen the domain so that key parts of it get pushed off the URL bar in mobile browsers.
To that end, he said, it makes perhaps the most sense to focus on new domain registrations that have encryption certificates tied to them, since the issuance of an SSL certificate for a domain is usually a sign that it is about to be put to use. As noted in previous stories here, roughly 75 percent of all phishing sites now have the padlock (start with “https://”), mainly because the major Web browsers display security alerts on sites that don’t.
Schwartzman said more domain registrars should follow the example of Los Angeles-based Namecheap Inc., which last month pledged to stop accepting the automated registration of website names that include words or phrases tied to the COVID-19 pandemic. Since then, a handful of other registrars have said they plan to manually review all such registrations going forward.
The Internet Corporation for Assigned Names and Numbers (ICANN), the organization that oversees the registrar industry, recently sent a letter urging registrars to be more proactive, but stopped short of mandating any specific actions.
Schwartzman called ICANN’s response “weak tea.”
“It’s absolutely ludicrous that ICANN hasn’t stepped up, and they will bear significant responsibility for any deaths that may happen as a result of all this,” Schwartzman said. “This is a CYA response at best, and dictates to no one that they should do anything.”
Michael Daniel, president of the Cyber Threat Alliance — a cybersecurity industry group that’s also been working to fight COVID-19 related fraud — agreed, saying more pressure needs to be applied to the registrar community.
“It’s really hard to do anything about this unless the registrars step up and do something on their own,” Daniel said. “It’s either that or the government gets involved. That doesn’t mean some [registrars] aren’t doing what they can, but in general what the industry is doing is nowhere near as fast as the bad guys are generating these domains.”
The U.S. government may well soon get more involved. Earlier this week, Senators Cory Booker (D-N.J.), Maggie Hassan (D-N.H.) and Mazie K. Hirono (D-Hawaii) sent letters to eight domain name company leaders, demanding to know what they were doing to combat the threat of malicious domains, and urging them to do more.
“As cybercriminals and other malevolent actors seek to take advantage of the Coronavirus pandemic, it is critical that domain name registrars like yours (1) exercise diligence and ensure that only legitimate organizations can register Coronavirus-related domain names and domain names referencing online communications platforms; (2) act quickly to suspend, cancel, or terminate registrations for domains that are involved in unlawful or harmful activity; and (3) cooperate with law enforcement to help bring to justice cybercriminals profiting from the Coronavirus pandemic,” the senators wrote.
from Krebs on Security https://krebsonsecurity.com/2020/04/sipping-from-the-coronavirus-domain-firehose/
Comments
Post a Comment