Krebs - UK Ad Campaign Seeks to Deter Cybercrime
The United Kingdom’s anti-cybercrime agency is running online ads aimed at young people who search the Web for services that enable computer crimes, specifically trojan horse programs and DDoS-for-hire services. The ad campaign follows a similar initiative launched in late 2017 that academics say measurably dampened demand for such services by explaining that their use to harm others is illegal and can land potential customers in jail.
For example, search in Google for the terms “booter” or “stresser” from a U.K. Internet address, and there’s a good chance you’ll see a paid ad show up on the first page of results warning that using such services to attack others online is illegal. The ads are being paid for by the U.K.’s National Crime Agency, which saw success with a related campaign for six months starting in December 2017.
A Google ad campaign paid for by the U.K.’s National Crime Agency.
NCA Senior Manager David Cox said the agency is targeting its ads to U.K. males age 13 to 22 who are searching for booter services or different types of remote access trojans (RATs), as part of an ongoing effort to help steer young men away from cybercrime and toward using their curiosity and skills for good. The ads link to advertorials and to the U.K.’s Cybersecurity Challenge, which tries gamify computer security concepts and highlight potential careers in cybersecurity roles.
“The fact is, those standing in front of a classroom teaching children have less information about cybercrime than those they’re trying to teach,” Cox said, noting that the campaign is designed to support so-called “knock-and-talk” visits, where investigators visit the homes of young people who’ve downloaded malware or purchased DDoS-for-hire services to warn them away from such activity. “This is all about showing people there are other paths they can take.”
While it may seem obvious to the casual reader that deploying some malware-as-a-service or using a booter to knock someone or something offline can land one in legal hot water, the typical profile of those who frequent these services is young, male, impressionable and participating in online communities of like-minded people in which everyone else is already doing it.
In 2017, the NCA published “Pathways into Cyber Crime,” a report that drew upon interviews conducted with a number of young men who were visited by U.K. law enforcement agents in connection with various cybercrime investigations.
Those findings, which the NCA said came about through knock-and-talk interviews with a number of suspected offenders, found that 61 percent of suspects began engaging in criminal hacking before the age of 16, and that the average age of suspects and arrests of those involved in hacking cases was 17 years old.
The majority of those engaged in, or on the periphery of, cyber crime, told the NCA they became involved via an interest in computer gaming.
A large proportion of offenders began to participate in gaming cheat websites and “modding” forums, and later progressed to criminal hacking forums.
The NCA learned the individuals visited had just a handful of primary motivations in mind, including curiosity, overcoming a challenge, or proving oneself to a larger group of peers. According to the report, a typical offender faces a perfect storm of ill-boding circumstances, including a perceived low risk of getting caught, and a perception that their offenses in general amounted to victimless crimes.
“Law enforcement activity does not act as a deterrent, as individuals consider cyber crime to be low risk,” the NCA report found. “Debrief subjects have stated that they did not consider law enforcement until someone they knew or had heard of was arrested. For deterrence to work, there must be a closing of the gap between offender (or potential offender) with law enforcement agencies functioning as a visible presence for these individuals.”
Cox said the NCA will continue to run the ads indefinitely, and that it is seeking funding from outside sources — including major companies in online gaming industry, whose platforms are perhaps the most targeted by DDoS-for-hire services. He called the program a “great success,” noting that in the past 30 days (13 of which the ads weren’t running for funding reasons), the ads generated some 5.32 million impressions, and more than 57,000 clicks.
FLATTENING THE CURVE
Richard Clayton is director of the University of Cambridge Cybercrime Centre, which has been monitoring DDoS attacks for several years using a variety of sensors across the Internet that pretend to be the types of systems which are typically commandeered and abused to help launch such assaults.
Last year, Clayton and fellow Cambridge researchers published a paper showing that law enforcement interventions — including the NCA’s anti-DDoS ad campaign between 2017 and 2018 — demonstrably slowed the growth in demand for DDoS-for-hire services.
“Our data shows that by running that ad campaign, the NCA managed to flatten out demand for booter services over that period,” Clayton said. “In other words, the demand for these services didn’t grow over the period as we would normally see, and we didn’t see more people doing it at the end of the period than at the beginning. When we showed this to the NCA, they were ever so pleased, because that campaign cost them less than ten thousand [pounds sterling] and it stopped this type of cybercrime from growing for six months.”
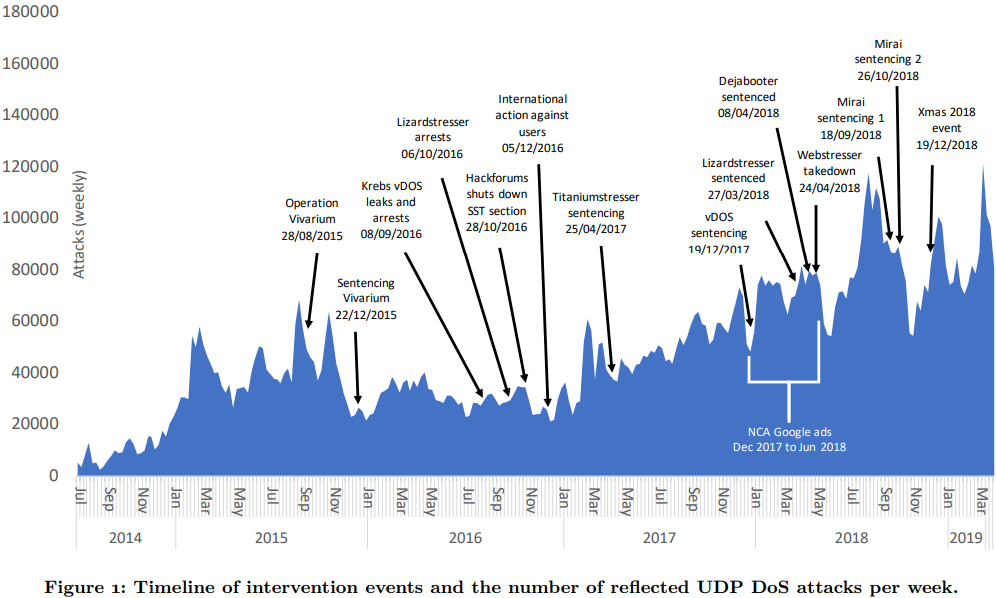
The Cambridge study found various interventions by law enforcement officials had measurable effects on the demand for and damage caused by booter and stresser services. Source: Booting the Booters, 2019.
Clayton said part of the problem is that many booter/stresser providers claim they’re offering lawful services, and many of their would-be customers are all too eager to believe this is true. Also, the price point is affordable: A typical booter service will allow customers to launch fairly high-powered DDoS attacks for just a few dollars per month.
“There are legitimate companies that provide these types of services in a legal manner, but there are all types of agreements that have to be in place before this can happen,” Clayton said. “And you don’t get that for ten bucks a month.”
DON’T BE EVIL
The NCA’s ad campaign is competing directly with Google ads taken out by many of the same people running these DDoS-for-hire services. It may surprise some readers to learn that cybercrime services often advertise on Google and other search sites much like any legitimate business would — paying for leads that might attract new customers.
Several weeks back, KrebsOnSecurity noticed that searching for “booter” or “stresser” in Google turned up paid ads for booter services prominently on the first page of results. But as I noted in a tweet about the finding, this is hardly a new phenomenon.
A booter ad I reported to Google that the company subsequently took offline.
Cambridge’s Clayton pointed me to a blog post he wrote in 2018 about the prevalence of such ads, which violate Google’s policies on acceptable advertisements via its platform. Google says it doesn’t allow ads for services that “cause damage, harm or injury,” and that they don’t allow adverts for services that “are designed to enable dishonest behavior.”
Clayton said Google eventually took down the offending ads. But as my few seconds of Googling revealed, the company appears to have decided to play wack-a-mole when people complain, instead of expressly prohibiting the placement of (and payment for) ads with these terms.
Google told KrebsOnSecurity that it relies on a combination of technology and people to enforce its policies.
“We have strict ad policies designed to protect users on our platforms,” Google said in a written statement. “We prohibit ads that enable dishonest behavior, including services that look to take advantage of or cause harm to users. When we find an ad that violates our policies we take action. In this case, we quickly removed the ads.”
Google pointed to a recent blog post detailing its enforcement efforts in this regard, which said in 2019 the company took down more than 2.7 billion ads that violated its policies — or more than 10 million ads per day — and that it removed a million advertiser accounts for the same reason.
The ad pictured above ceased to appear shortly after my outreach to them. Unfortunately, an ad for a different booter service (shown below) soon replaced the one they took down.
An ad for a DDoS-for-hire service that appeared shortly after Google took down the ones KrebsOnSecurity reported to them.
from Krebs on Security https://krebsonsecurity.com/2020/05/uk-ad-campaign-seeks-to-deter-cybercrime/
Comments
Post a Comment