Krebs - USPS Site Exposed Data on 60 Million Users
U.S. Postal Service just fixed a security weakness that allowed anyone who has an account at usps.com to view account details for some 60 million other users, and in some cases to modify account details on their behalf.

Image: USPS.com
KrebsOnSecurity was contacted last week by a researcher who discovered the problem, but who asked to remain anonymous. The researcher said he informed the USPS about his finding more than a year ago yet never received a response. After confirming his findings, this author contacted the USPS, which promptly addressed the issue.
The problem stemmed from an authentication weakness in a USPS Web component known as an “application program interface,” or API — basically, a set of tools defining how various parts of an online application such as databases and Web pages should interact with one another.
The API in question was tied to a Postal Service initiative called “Informed Visibility,” which according to the USPS is designed to let businesses, advertisers and other bulk mail senders “make better business decisions by providing them with access to near real-time tracking data” about mail campaigns and packages.
In addition to exposing near real-time data about packages and mail being sent by USPS commercial customers, the flaw let any logged-in usps.com user query the system for account details belonging to any other users, such as email address, username, user ID, account number, street address, phone number, authorized users, mailing campaign data and other information.
Many of the API’s features accepted “wildcard” search parameters, meaning they could be made to return all records for a given data set without the need to search for specific terms. No special hacking tools were needed to pull this data, other than knowledge of how to view and modify data elements processed by a regular Web browser like Chrome or Firefox.
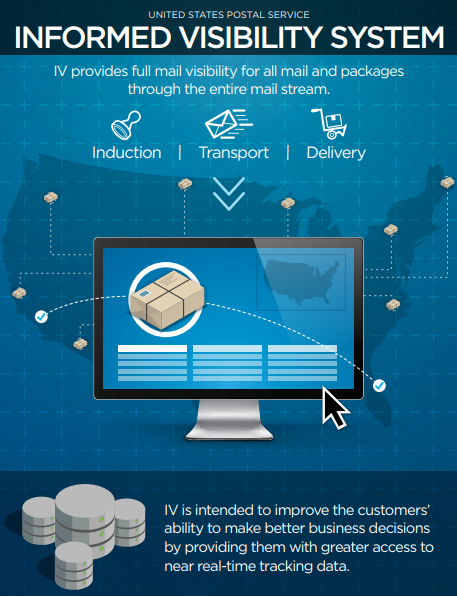
A USPS brochure advertising the features and benefits of Informed Visibility.
In cases where multiple accounts shared a common data element — such as a street address — using the API to search for one specific data element often brought up multiple records. For example, a search on the email addresses for readers who volunteered to help with this research turned up multiple accounts when those users had more than one user signed up at the same physical address.
“This is not good,” said one anonymous reader who volunteered to help with this research, after viewing a cut-and-paste of his USPS account details looked up via his email address. “Especially since we moved due to being threatened by a neighbor.”
Nicholas Weaver, a researcher at the International Computer Science Institute and lecturer at UC Berkeley, said the API should have validated that the account making the request had permission to read the data requested.
“This is not even Information Security 101, this is Information Security 1, which is to implement access control,” Weaver said. “It seems like the only access control they had in place was that you were logged in at all. And if you can access other peoples’ data because they aren’t enforcing access controls on reading that data, it’s catastrophically bad and I’m willing to bet they’re not enforcing controls on writing to that data as well.”
A cursory review by KrebsOnSecurity indicates the promiscuous API let any user request account changes for any other user, such as email address, phone number or other key details.
Fortunately, the USPS appears to have included a validation step to prevent unauthorized changes — at least with some data fields. Attempts to modify the email address associated with my USPS account via the API prompted a confirmation message sent to the email address tied to that account (which required clicking a link in the email to complete the change).
It does not appear USPS account passwords were exposed via this API, although KrebsOnSecurity conducted only a very brief and limited review of the API’s rather broad functionality before reporting the issue to the USPS. The API at issue resides here; a copy of the API prior to its modification on Nov. 20 by the USPS is available here as a text file.
The ability to modify database entries related to Informed Visibility user accounts could create problems for the USPS’s largest customers — think companies like Netflix and others that get discounted rates for high volumes. For instance, the API allowed any user to convert regular usps.com accounts to Informed Visibility business accounts, and vice versa.
Spammers and email scam artists also could have a field day with this USPS vulnerability, said Robert Hansen, chief technology officer at Bit Discovery, a security firm in Austin, Texas.
“This could easily be leveraged to build up mass targeted spam or spear phishing,” Hansen said. “It should have been protected via authentication and validated against the logged in user in question.”
According to a somewhat redacted vulnerability assessment of Informed Visibility (PDF) published in October 2018 by the USPS’s Office of Inspector General (OIG), auditors found a number of authentication and encryption weaknesses in the service. But they seemed to have overlooked this rather glaring security problem. The USPS told the OIG it had addressed the authentication problems raised in the audit report, which appear to have been related to how data was encrypted in transit.
The API vulnerability is the latest security stumble for the Postal Service’s efforts to modernize operations. The Informed Visibility program is the sister initiative to the USPS’s Informed Delivery service, which lets residents view scanned images of all incoming mail. The API vulnerability affected all usps.com users, including some 13 million Informed Delivery users.
As detailed in numerous stories here, Informed Delivery has struggled to implement security features that might prevent abuse of the system by identity thieves and other ne’er-do-wells.
Earlier this month, KrebsOnSecurity broke the news that the U.S. Secret Service issued an internal memo about identity thieves abusing Informed Delivery to aid in mail theft. The story cited cases in multiple states involving scammers who ordered new credit cards in the names of victims, and then signed up as those victims at Informed Delivery once the cards were sent — thereby allowing the thieves to tell exactly when the new credit cards would be arriving in the mail.
Although fixing information disclosure and authentication weaknesses is often quite simple, it’s remarkable how many organizations that should know better don’t invest the resources needed to find and address them. In September, this author detailed how a company used by thousands of state and local governments to accept online payments was leaking more than 14 million records.
In August, KrebsOnSecurity disclosed a similar flaw at work across hundreds of small bank Web sites run by Fiserv, a major provider of technology services to financial institutions.
In July, identity theft protection service LifeLock corrected an information disclosure flaw that exposed the email address of millions of subscribers. And in April 2018, PaneraBread.com remedied a weakness exposing millions of customer names, email and physical addresses, birthdays and partial credit card numbers.
Got a tip about a security vulnerability similar to those detailed above, or perhaps something more serious? Please drop me a note at krebsonsecurity @ gmail.com.
from Krebs on Security https://krebsonsecurity.com/2018/11/usps-site-exposed-data-on-60-million-users/
Comments
Post a Comment