Krebs - International Action Targets Emotet Crimeware
Authorities across Europe on Tuesday said they’d seized control over Emotet, a prolific malware strain and cybercrime-as-service operation. Investigators say the action could help quarantine more than a million Microsoft Windows systems currently compromised with malware tied to Emotet infections.
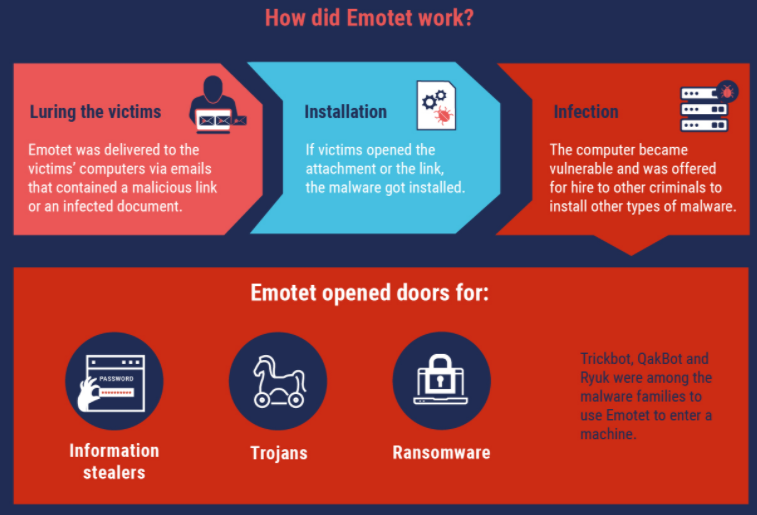
First surfacing in 2014, Emotet began as a banking trojan, but over the years it has evolved into one of the more aggressive platforms for spreading malware that lays the groundwork for ransomware attacks.
In a statement published Wednesday morning on an action dubbed “Operation Ladybird,” the European police agency Europol said the investigation involved authorities in the Netherlands, Germany, United States, the United Kingdom, France, Lithuania, Canada and Ukraine.
“The EMOTET infrastructure essentially acted as a primary door opener for computer systems on a global scale,” Europol said. “Once this unauthorised access was established, these were sold to other top-level criminal groups to deploy further illicit activities such data theft and extortion through ransomware.”
Experts say Emotet is a pay-per-install botnet that is used by several distinct cybercrime groups to deploy secondary malware — most notably the ransomware strain Ryuk and Trickbot, a powerful banking trojan. It propagates mainly via malicious links and attachments sent through compromised email accounts, blasting out tens of thousands of malware-laced missives daily.
Emotet relies on several hierarchical tiers of control servers that communicate with infected systems. Those controllers coordinate the dissemination of second-stage malware and the theft of passwords and other data, and their distributed nature is designed to make the crimeware infrastructure more difficult to dismantle or commandeer.
In a separate statement on the malware takeover, the Dutch National police said two of the three primary servers were located in the Netherlands.
“A software update is placed on the Dutch central servers for all infected computer systems,” the Dutch authorities wrote. “All infected computer systems will automatically retrieve the update there, after which the Emotet infection will be quarantined. Simultaneous action in all the countries concerned was necessary to be able to effectively dismantle the network and thwart any reconstruction.”
A statement from the German Federal Criminal Police Office about their participation in Operation Ladybird said prosecutors seized 17 servers in Germany that acted as Emotet controllers.
“As part of this investigation, various servers were initially identified in Germany with which the malicious software is distributed and the victim systems are monitored and controlled using encrypted communication,” the German police said.
Sources close to the investigation told KrebsOnSecurity the law enforcement action included the arrest of several suspects in Europe thought to be connected to the crimeware gang, although that could not be confirmed. The core group of criminals behind Emotet are widely considered to be operating out of Russia.
A video released to YouTube by the National Police of Ukraine this morning shows authorities there raiding a residence, seizing cash and computer equipment, and what appear to be numerous large bars made of gold.

Police in the Netherlands seized huge volumes of data stolen by Emotet infections, including email addresses, usernames and passwords. A tool on the Dutch police website lets users learn if their email address has been compromised by Emotet.
But because Emotet is typically used to install additional malware that gets its hooks deeply into infected systems, cleaning up after it is going to be far more complicated and may require a complete rebuild of compromised computers.
The U.S. Cybersecurity & Infrastructure Security Agency has labeled Emotet “one of the most prevalent ongoing threats” that is difficult to combat because of its ‘worm-like’ features that enable network-wide infections.” Hence, a single Emotet infection can often lead to multiple systems on the same network getting compromised.
It is too soon to say how effective this operation has been in fully wresting control over Emotet, but a takedown of this size is a significant action.
In October, Microsoft used trademark law to disrupt the Trickbot botnet. Around the same time, the U.S. Cyber Command also took aim at Trickbot. However, neither of those actions completely dismantled the crimeware network, which remains in operation today.
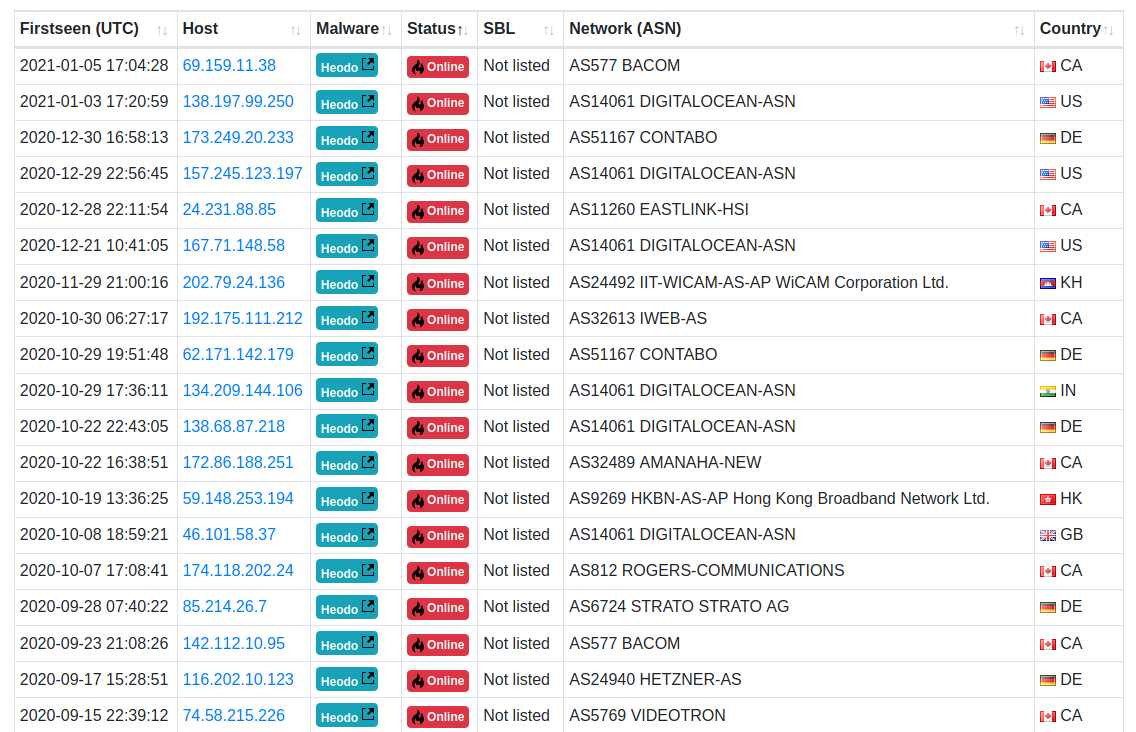
Roman Hüssy, a Swiss information technology expert who maintains Feodotracker — a site that lists the location of major botnet controllers — told KrebsOnSecurity that prior to January 25, some 98 Emotet control servers were active. The site now lists 20 Emotet controllers online, although it is unclear if any of those remaining servers have been commandeered as part of the quarantine effort.
from Krebs on Security https://krebsonsecurity.com/2021/01/international-action-targets-emotet-crimeware/
Comments
Post a Comment